8 Essential Secure Java 8 Coding Practices

In this article, we embark on a journey into the realm of secure coding in Java 8, where we unravel the key practices that will fortify your code against malicious exploits and protect your applications from the evolving landscape of cyber threats. Writing secure code is not just an option; it's a necessity. In this deep dive, we dive headfirst into the world of Java 8 and its powerful features, uncovering the essential practices that will elevate your code to a new level of robustness and resilience.
From input validation and least privilege principles to defense in depth and secure use of libraries, we leave no stone unturned in our quest to equip you with the tools and knowledge to build secure Java applications. Let's dive in!
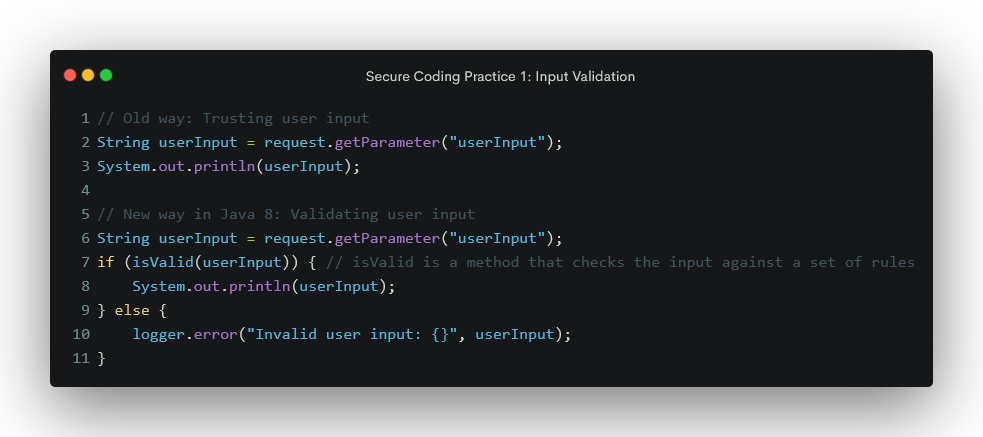
Secure Coding Practice 1: Input Validation
Never trust user input blindly. Always validate and sanitize it before use. This can help prevent attacks such as SQL injection and cross-site scripting (XSS). Use regular expressions to check for specific types of malicious input, use a whitelist of allowed characters, and sanitize the input before use.
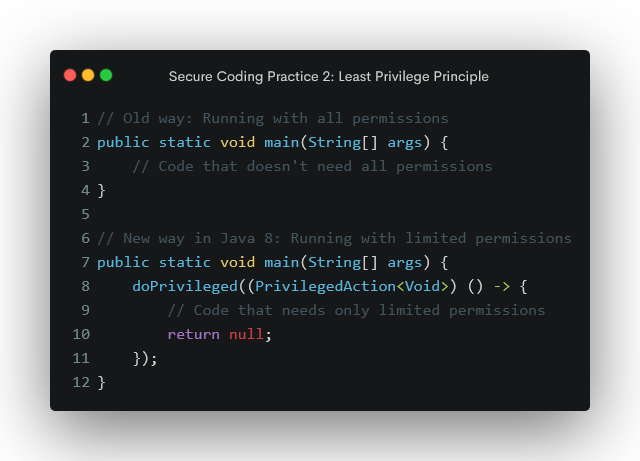
Secure Coding Practice 2: Least Privilege Principle
Give your code only the permissions it needs to perform its job, nothing more. This limits the potential damage in case of a security breach. Use role-based access control (RBAC) to assign permissions to users and groups, use least privilege by default, and use least privilege for temporary tasks and remote access.
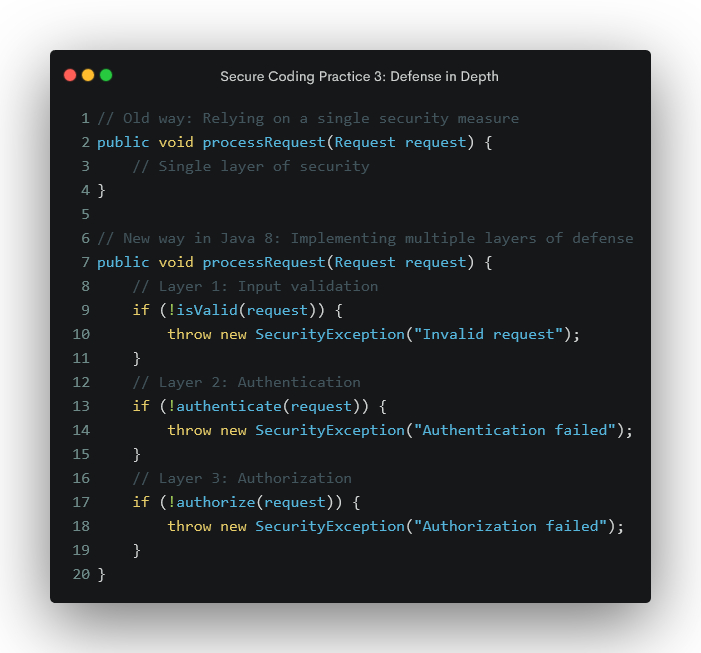
Secure Coding Practice 3: Defense in Depth
Don't rely on a single security measure. Implement multiple layers of defense to ensure that if one layer is breached, others still stand. Use a variety of security measures, use different security measures for different layers of defense, use security measures that complement each other, and use security measures that are regularly updated.
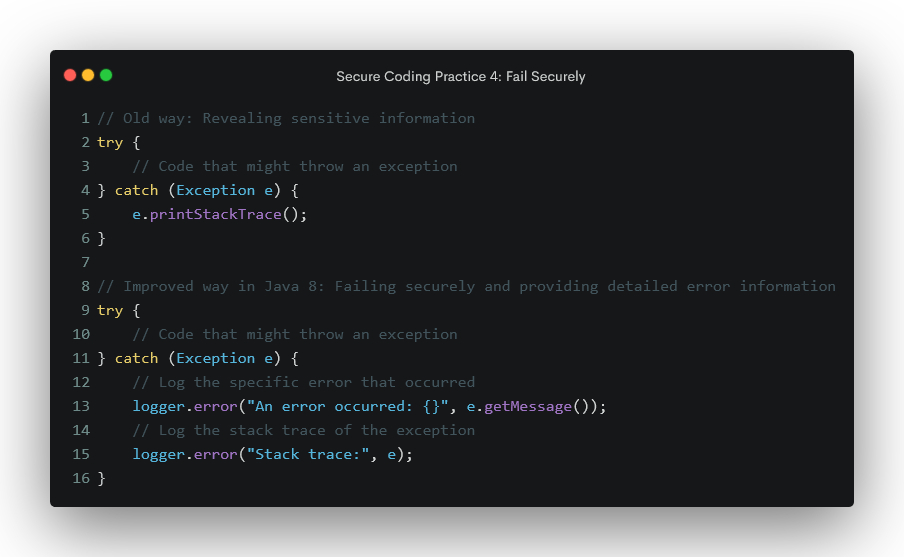
Secure Coding Practice 4: Fail Securely
Design your code to fail securely. In case of an error, it should not leave the system in a vulnerable state or reveal sensitive information. Do not log sensitive information, such as the stack trace of the exception. Log the specific error that occurred, log the stack trace of the exception to a file or database, do not retry the operation if it fails, and handle different types of exceptions.
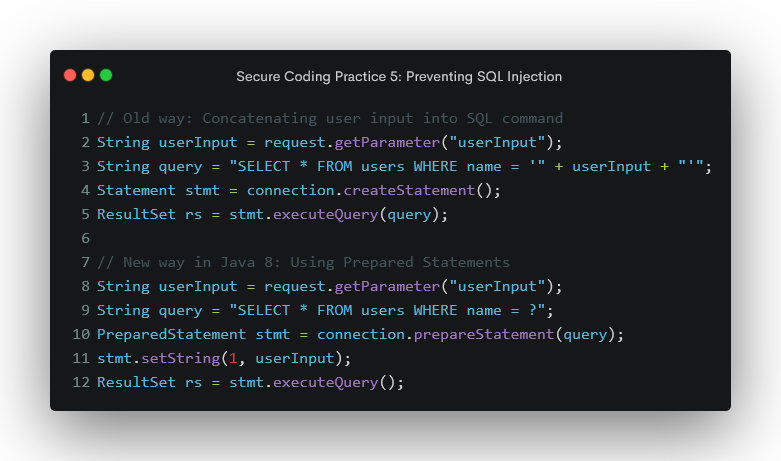
Secure Coding Practice 5: Preventing SQL Injection
SQL Injection is a common attack where an attacker manipulates your SQL queries by injecting malicious SQL code through user inputs. To prevent SQL Injection, do not concatenate user input into SQL commands, use prepared statements, sanitize user input before using it in SQL queries, and use a database firewall to filter malicious SQL queries.
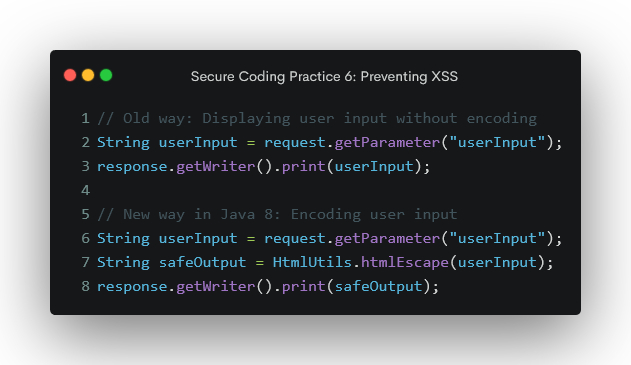
Secure Coding Practice 6: Preventing Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is an attack where an attacker injects malicious scripts into web pages viewed by other users. To prevent XSS, encode user input before displaying it on your web pages, use a web application firewall (WAF) to filter malicious XSS scripts, and educate your users about XSS attacks and how to avoid them.
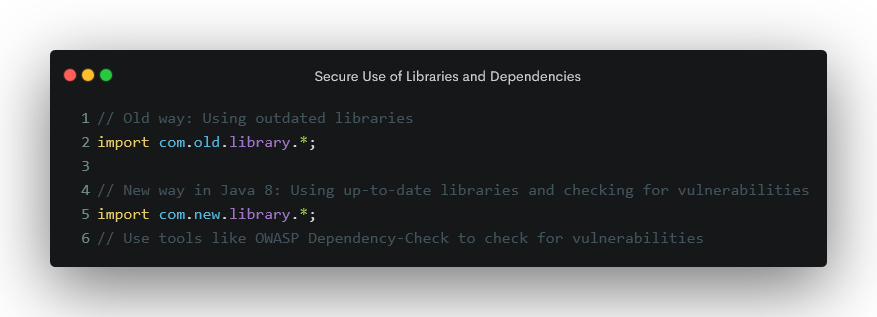
Secure Coding Practice 7: Secure Use of Libraries and Dependencies
Third-party libraries and dependencies can greatly speed up development, but they can also introduce security risks if not used properly. Use only libraries from trusted sources, keep your libraries up-to-date, and use tools like OWASP Dependency-Check to check for vulnerabilities.
Secure Coding Practice 8: Security Testing and Tools
Last but not least, never underestimate the importance of security testing. Use a variety of tools, use different tools for different types of security testing, and use tools that are regularly updated. Static code analyzers, vulnerability scanners, and penetration testing can help find and fix security issues before they cause harm.
Next Steps
We've reached the end of our Java 8 Security Deep Dive, where we've explored the eight essential secure coding practices that will fortify your Java applications and protect them from malicious exploits. Throughout our journey, we've learned to validate inputs, embrace the least privilege principle, implement defense in depth, fail securely, prevent SQL injection and cross-site scripting, use libraries securely, and leverage security testing tools. These practices, when applied diligently, will empower you to build robust, resilient, and secure Java applications that instill confidence in your users.
Remember, secure coding is not a one-time endeavor but an ongoing commitment. As the threat landscape evolves, so must our defenses. Stay vigilant, keep yourself updated with the latest security practices, and adopt a proactive approach to secure coding.